AIM has been educated, advocating and advancing RFID through the RFID Experts Group for 20 + years! Watch this video to get a better idea on how the REG enables adoption of RFID technologies worldwide!
Active Tags
Tags which use batteries as a partial or complete source of power. They are further differentiated by separating them into those with replaceable batteries and those which have the batteries inside a sealed unit or what may be termed unitized active tags.
Addressability
The ability to address bits, fields, files or other portions of the storage in a tag.
Alignment
The orientation of the tag to the reader in pitch, roll, and yaw.
Antenna
Antennas are the conductive elements which radiate, and/or receive energy in the radio frequency spectrum, to and from the tag.
Bidirectional
Capable of operating in either of two directions which are the opposite of each other. For example, a tag which can be read or written from either side is bi-directional.
Backscatter Tags
An amplitude modulation communication method used by a non-transponder RFID tag. The carrier signal (from the reader) is shunted through a transistor, causing a slight load on the carrier signal. This produces fluctuations in it’s amplitude and the reader experiences a momentary voltage drop. This amplitude-modulation loading of the reader’s transmitted field provides a communication path back to the reader.
Capacity
The number of bits or bytes that can be programmed into a tag. This may represent the bits accessible to the user or the total number including those reserved to the manufacturer e.g. parity or control bits.
Capture Window/Field
Region of the scanner field in which a tag will operate.
Closed Systems
A system in which relevant data regarding the attributes of the object is stored in a common data base, accessible via data link by referencing the individual ID code. It usually refers to a system under the control of a single owner or authority.
Code Plate
See “Tag”
Controller
See “Multiplexer”
Electromagnetic Coupling
Systems which in use a magnetic field as a means of transferring data or power are said to use a electromagnetic coupling.
Electronic Label
See “Tag”
Electrostatic coupling
Systems which use the inducing of a voltage on a plate as a means of transferring data or power are said to use electrostatic coupling.
EPC® (Electronic Product Code)
An item identification system based on RFID that includes technical specifications for the RFID system plus a structure and syntax for company identification codes, item naming conventions, and web-based distributed data bases. Jointly administered by the Uniform Code Council and EAN International.
Error
Any operation or data which is not in accord with the design or input to the system.
Error Correcting Code (ECC)
Supplemental bits in a data transfer used in conjunction with a polynomial algorithm, in order to compute the value of missing or erroneous data bits (e.g. for a 32 bit data transmission, 7 additional bits are required.)
Error Correcting Mode
Mode of data communication in which missing or erroneous bits are automatically corrected.
Error Correcting Protocol
The rules by which the error correcting mode operates.
Error Management
Techniques used to ensure that only correct information is presented to the user of the system.
Error Rate
The number of errors per number of transactions.
Exciter
The electronics which drive an antenna are called the exciter or transmitter. Together with the antenna they are called a scanner.
Expansion Port
A plug accessing additional 1/0 capability on a computer or peripheral device.
Factory Programming
The programming of information into a tag occurring as part of the manufacturing process resulting in a read only tag.
Field Programming
Programming information into the tags may occur after the tag has been shipped from the manufacturer to an OEM customer or end user or in some cases to the manufacturer’s distribution locations. Field programming usually occurs before the tag is installed on the object to be identified. This approach enables the introduction of data relevant to the specifics of the application into the tag at any time; however, the tag would typically have to be removed from its object. In some cases, change or duplication of all data in the tag is possible. In other cases, some portion is reserved for factory programming. This might include a unique tag serial number, for example.
Field Protection
The ability to limit the operations which can be performed on portions or fields of the data stored in a tag.
Flat Panel Antenna
Flat, conductive sheet antennas, usually made of metal plate or foil.
Frequency
The number of times a signal executes a complete excursion through its maximum and minimum values and returns to the same value (e.g. cycles).
I.D. Filter
Software that compares a newly read ID with those in a data base or set.
Inductive Coupling
Systems which use the inducing of a current in a coil as a means of transferring data or power are said to use inductive coupling (see illustration).
In Use Programming
Many applications require that new data or revisions to data already in the tag, be entered into the tag, while it remains attached to its object. The ability to read from and write data to the tag while attached to its object is called in-use programming. Tags and systems with this capability are called read/write tags and systems.
Interrogator
See Reader and Programmer
ISM Band
A portion of the radio spectrum designated for Industrial, Scientific, Medical use.
Life
Functional period within which no maintenance, adjustment or repair is to be reasonably expected.
Memory Cards
A read/write or reprogrammable tag in credit card size.
Memory Modules
A read/write or reprogrammable tag.
Misread
A condition that exists when the data presented by the reader is different from the corresponding data in the tag.
Mobile Inventory Vehicle
Vehicle equipped with a system for locating tagged vehicles, containers, and other objects for the purpose of inventory control.
Modulation
The methods of modulating or altering the carriers in order to carry the encoded information are quite varied. They include amplitude modulation (AM)/ phase modulation (PM), frequency modulation (FM), frequency shift keyed (FSK), pulse position (PPM), pulse duration (PDM) and continuous wave (CW). In some cases, different modulating techniques are used in each direction (to and from the tags).
Modulation, amplitude (AM)
Data is contained in changes in amplitude of the carrier.
Modulation, phase (PM)
Data is contained in the changes in the phase of the carrier.
Modulation, frequency (FM)
Data is contained in the changes in the frequency of the carrier.
Modulation, frequency shift keyed (FSK)
Data is contained in the changes between two frequencies of carrier.
Modulation, pulse duration (PDM)
Data is contained in the duration of pulses.
Modulation, pulse position (PPM)
Data is contained in the position of pulses relative to a reference point.
Modulation, continuous wave (CW)
Data is contained in a carrier which is switched on and off.
Multiplexer (multiplexor)
A device which supports multiple scanners or antennas by checking each in accordance with some scheduling scheme which may be either round robin or priority based. This reduces the total amount of electronics in the system at the expense of having all scanners being “blind” part of the time. These devices are called multiplexers or multichannel readers or just controllers.
Nominal
The value at which a system is designed assure optimal operation. Tolerance consider the “normal” deviation of variable factors.
Nominal Range
The range at which a systems can assure reliable operation, considering the normal variability of the environment in which it is used.
Omnidirectional
Capability of a tag to operate in any orientation.
Open Systems
Application in which reader/writers do not have access to a common data base.
Orientation
Alignment of the tag with respect to the scanner, measured in pitch, roll, and yaw.
Orientation Sensitivity
The degree to which the interrogation field and tag must be in alignment. The degree range is decreased by non-optimal orientation.
Passive Tags
Passive tags contain no internal power source. They are externally powered and typically derive their power from the carrier signal radiated from the scanner.
Port Concentrator
A device that accepts the output from a number of communication interfaces and introduces them into a communication network.
Power Levels
Levels of power radiated from a scanner or tag, usually measured in volts/meter.
Programming
Adding data to or altering data in a tag.
Programmability
In order to be identifiers of specific objects, tags must at some point have their identity and/or other data entered into them. This capability is called programmability.
Programmer
Some tags which can have their contents changed by a set of electronics in close proximity or in electrical contact with it. Those electronics and their packaging are called a programmer.
Projected Life
This is defined in terms of number of read and/or write cycles, or in active tags this may include shelf life.
Propogation coupling
Systems which use the propogation of radio waves as a means of transferring data or power are said to use propogation coupling (see illustration).
Proximity sensor
A device that detects and signals the presence of a selected object at or near the sensor’s location.
Reader
See “Scanner”
RF/DC
See “Wireless LAN”
RFlD
Systems that read or write data to RF tags that are present in a radio frequency field projected from RF reading/writing equipment. Data may be contained in one (1 ) or more bits for the purpose of providing identification and other information relevant to the object to which the tag is attached. It incorporates the use of electromagnetic, or electrostatic coupling in the radio frequency portion of the spectrum to communicate to or from a tag through a variety of modulation and encodation schemes.
RF/AIS
Radio Frequency Automatic Identification Systems. See “RFID.”
Range
The distance at which successful reading and/or writing can be accomplished.
Read
The decoding, extraction and presentation of data from formatting, control and error management bits sent from a tag.
Read Only
See ”WORM”
Readability
The ability to extract data under less than optimal conditions.
Read Rate
The maximum rate at which data can be read from a tag expressed in bits or bytes per second.
Read/Write
Many applications require that new data or revisions to data already in the Tag, be entered into the Tag, while it remains attached to its object. Tags with this capability are said to be reprogrammable and are called read/write tags, memory cards or memory modules.
Reader
The device containing the digital electronics which extract and separate the information from the format definition and error management bits. The digital electronics perform the actual reading function. These read electronics may also interface to an integral display and/or provide a parallel or serial communications interface to a host computer or industrial controller.
Reader/Writer
The set of electronics can change the contents of tags while they remain attached to their object are called a reader/writer. (See also reader).
Reprogrammable
Many applications require that new data or revisions to data already in the tag, be entered into the tag, while it remains attached to its object. The ability to read from and write data to the tag while attached to its object is called in-use programming. Tags with this capability are said to be re-programmable and are called read/write tags, memory cards or memory modules.
Rewritable
See “Reprogrammable”
SAW
Surface Acoustic Wave. A technology in which radio frequency signals are converted to acoustic signals in a piezolectric crystalline material. Variations in phrase shift ion the reflected signal can be used to provide a unique identity.
Scanner
The antenna’s, transmitter (or exciter) and receiver electronics integrated in a single package called the scanner. They may be combined with additional digital electronics including a microprocessor in a package called a reader.
Semi-Passive Tags
RFID tags that contain a battery to power sensors or other devices connected to a passive RFID tag.
Sensor
A device that responds to a physical stimulus and produces an electronic signal. See also “Scanner.“
Separation
Operational distance between two tags.
Signaling Technique
A complete description of the modulation, encodation, protocol, and sequences required to communicate between two elements of a system.
Smart Labels
The term applied to relatively inexpensive passive RFID tags typically embedded in a self-adhesive paper or similar label such as those used for bar codes or shipping labels.
Speed
The rate at which something occurs, typically referring to the rate of data transfer during reading or writing. Speed may also refer to the maximum speed of the tag relative to the reader when read or write operations can be successfully performed (often dependent on the amount of data to be read or written).
Spread Spectrum
A method of broadcasting data on a number of frequencies in a band, either sequentially or in parallel, to avoid interference and ensure successful data communications.
Tag
The data carrier in an RFID system that communicates with the reader. Tags may be based on transponder, backscatter, or SAW technology and may be passive, semi-passive, or active.
TAV (Total Asset Visibility)
A supply chain initiative by the U.S. Department of Defense to identify and track all assets from initial shipment through to eventual disposal. Much of the TAV program is based on the use of both active and passive RFID.
Transponder
The transmitter/receiver pair or transceiver plus the information storage mechanism attached to the object is referred to as the tag, transponder, electronic label, code plate and various other terms. Although transponder is technically the most accurate, the most common term and the one preferred by the Automatic Identification Manufacturers is transponder tag.
UHF
RFID systems that operate in approximately the 900 MHz range.
Verify
To assure that the intended operation was correctly performed.
Wireless LAN (Local Area Network)
Systems which communicate over a radio link between a host computer and a data source e.g. keyboards, data terminals, readers for OCR, Bar Codes, Mag Stripes, RF/ID etc. WLANs enhances the capabilities of Automatic ID Systems by providing the capabilities of hard wired data communications without the physical restrictions interconnecting wires.
WORM (Write Once Read Many)
Tags that, once written to, cannot be rewritten or changed. See also: “Field Programming” and “Factory Programming.” Also called “Read Only.”
Write
The transfer of data to a tag, the tags internal operation of storing the data and it may include reading the data in order to verify the operation.
Write Rate
The rate at which information is transferred to a tag, written into the tag’s memory and verified as being correct. It is quantified as the average number of bits or bytes per second in which the complete transaction can be performed.
Implementing RFID is a Business Decision, Not a Technology Question
Obfuscate Me with Facts
According to Merriam-Webster’s Dictionary, “obfuscate” means 1 a : darken, b : to make obscure, 2 : confuse.
And that is exactly what often happens in considering RFID.
You should, by now, be familiar with the benefits of RFID: non-contact, non-line-of-sight reading, read/write capability, etc.
The problem is that different RFID systems have different capabilities and costs.
Not all tags, for example, are read/write. Some tags are active, some are passive some are semi-passive. They don’t all have the same data capacity or range. Similarly, the different operating frequencies don’t offer the same range or data transfer rates. And not all frequencies are legal in all countries.
Nonetheless, we often find hopeful stories that conglomerate all the best features of every available system into an imaginary product that, in the words of Dr. David Allais, “does everything, costs nothing and fits on the head of a pin.” (At the time, Dr. Allais was referring to bar codes, but the analogy is perhaps even more appropriate for RFID.)
Many companies, nonetheless, are waiting for this mythical system to be made available. And a common perception is that it will be “some time early next year” — whenever “next year” happens to be.
Waiting for this system to be announced is rather like waiting for Elvis to reappear.
Time to Step Back
It is time to stop focusing on both costs and benefits and start looking at solving business process problems.
When we evaluate RFID for a given application, we need to start with the basics.
- What data do we need to encode?
- Where will the data be read?
- Are there physical or environmental constraints where the data must be read?
- Must the object be moving when read? If so, how fast?
- What is the required read range?
- How often will the data need to be read?
- Do we need (want) to enable unattended operation?
So far, this list could be used to evaluate the applicability of almost any AIDC technology. Two-dimensional bar codes certainly offer expanded data capacity, fairly high reading speed and range and can be configured for unattended operation. So far, if the data is to be read only a few times and there are no significant environmental concerns, a bar code may be the more cost-effective solution.
In other words, we haven’t necessarily built a case for RFID yet.
So let’s look at some questions that might suggest RFID.
- Do we need (want) to write data back to the data carrier?
- Will the data carrier be embedded or otherwise not visible?
- Will the data carrier be subjected to surface contamination (e.g., paint, dirt)?
- Do we need to be able to read multiple data carriers at the same time?
If we answer yes to any of these questions, then we have established some rationale for using RFID.
Why? Because only RFID can meet our requirements.
Price, Cost and ROI
While companies have to justify an acceptable ROI for the costs associated with implementing RFID, they often overlook the price of not implementing it.
Some considerations:
- Will profitability eventually decrease if the status quo is maintained?
- Will the company lose a potential competitive advantage?
- Will the company eventually lack sufficient accurate information about its processes or inventory to effectively manage its business?
- Will customers’ perception of the company suffer?
- Will the company be able to catch up once competitors implement RFID?
- Will existing inefficiencies become unmanageable as the pace of business continues to increase?
- Not to be entirely negative, you also want to ask this question:
- Will RFID enhance your company’s ability to serve its customers? Improved customer service and customer loyalty are sometimes difficult to quantify. Sometimes it is easier to look at the negative side to understand the value of customer service. In other words:
- What is the cost of losing a customer to a competitor that offers better service?
Certainly not all these questions apply to all companies. They’re presented to stimulate your thinking about your own company and its competitive situation in the marketplace.
Notice, however, that the questions are not focused on the technology but rather on business processes, margins and competitive strength.
In the final analysis, it’s not about the cost of the tags. It’s about staying in — and ahead of — the game.
Components
A basic Radio Frequency Identification (RFID) system consists of three components:
- An antenna or coil
- A transceiver (with decoder)
- A transponder (RF tag) electronically programmed with unique information
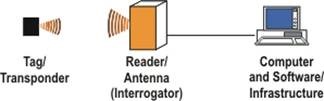
- The antenna emits radio signals to activate the tag and to read and write data to it.
- The reader emits radio waves in ranges of anywhere from one inch to 100 feet or more, depending upon its power output and the radio frequency used. When an RFID tag passes through the electromagnetic zone, it detects the reader’s activation signal.
- The reader decodes the data encoded in the tag’s integrated circuit (silicon chip) and the data is passed to the host computer for processing.
The purpose of an RFID system is to enable data to be transmitted by a portable device, called a tag, which is read by an RFID reader and processed according to the needs of a particular application. The data transmitted by the tag may provide identification or location information, or specifics about the product tagged, such as price, color, date of purchase, etc. RFID technology has been used by thousands of companies for a decade or more. . RFID quickly gained attention because of its ability to track moving objects. As the technology is refined, more pervasive – and invasive – uses for RFID tags are in the works.
A typical RFID tag consists of a microchip attached to a radio antenna mounted on a substrate.
A RFID microchip consists of three main functional blocks, a RF front-end, a RFID protocol controller and a non-volatile memory “NVM”. The RF front-end performs several key functions; interface to the antenna, RF energy harvesting and RF signal demodulation/decoding and encoding/modulation. The RFID protocol controller processes the decoded RF data, performs the functions as defined by the RFID air protocol, reading and writing to and from the NVM and generating unencoded RF transmit data. The NVM provides permanent storage of data as defined in the RFID protocol standard. The NVM may be small, storing as few as 64bits of protocol data, or large, storing in excess of 2Kbits (2048 bits). Very large memory RFID IC’s can use NVM blocks which can store up to 4Kbytes (32768 bits).
RFID tags are categorized as either active or passive. Active RFID tags are powered by an internal battery and are typically read/write, i.e., tag data can be rewritten and/or modified. An active tag’s memory size varies according to application requirements; some systems operate with up to 1MB of memory. In a typical read/write RFID work-in-process system, a tag might give a machine a set of instructions, and the machine would then report its performance to the tag. This encoded data would then become part of the tagged part’s history. The battery-supplied power of an active tag generally gives it a longer read range. The trade off is greater size, greater cost, and a limited operational life (which may yield a maximum of 10 years, depending upon operating temperatures and battery type).
Passive RFID tags operate without a separate external power source and obtain operating power generated from the reader. Passive tags are consequently much lighter than active tags, less expensive, and offer a virtually unlimited operational lifetime. The trade off is that they have shorter read ranges than active tags and require a higher-powered reader. Read-only tags are typically passive and are programmed with a unique set of data (usually 32 to 128 bits) that cannot be modified. Read-only tags most often operate as a license plate into a database, in the same way as linear barcodes reference a database containing modifiable product-specific information.
RFID systems are also distinguished by their frequency ranges. Low-frequency (30 KHz to 500 KHz) systems have short reading ranges and lower system costs. They are most commonly used in security access, asset tracking, and animal identification applications. High-frequency (850 MHz to 950 MHz and 2.4 GHz to 2.5 GHz) systems, offering long read ranges (greater than 90 feet) and high reading speeds, are used for such applications as railroad car tracking and automated toll collection. However, the higher performance of high-frequency RFID systems incurs higher system costs.
To retrieve the data stored on an RFID tag, you need a reader. A typical reader is a device that has one or more antennas that emit radio waves and receive signals back from the tag. The reader then passes the information in digital form to a computer system.
The significant advantage of all types of RFID systems is the noncontact, non-line-of-sight nature of the technology. Tags can be read through a variety of substances such as snow, fog, ice, paint, crusted grime, and other visually and environmentally challenging conditions, where barcodes or other optically read technologies would be useless. RFID tags can also be read in challenging circumstances at remarkable speeds, in most cases responding in less than 100 milliseconds. The read/write capability of an active RFID system is also a significant advantage in interactive applications such as work-in-process or maintenance tracking. Though it is a costlier technology (compared with barcode), RFID has become indispensable for a wide range of automated data collection and identification applications that would not be possible otherwise.
Developments in RFID technology continue to yield larger memory capacities, wider reading ranges, and faster processing. It is highly unlikely that the technology will ultimately replace barcode — even with the inevitable reduction in raw materials coupled with economies of scale, the integrated circuit in an RF tag will never be as cost-effective as a barcode label. However, RFID will continue to grow in its established niches where barcode or other optical technologies are not effective. If some standards commonality is achieved – whereby RFID equipment from different manufacturers can be used interchangeably – the market will very likely grow exponentially.
Current and Potential Uses of RFID
Asset Tracking
It’s no surprise that asset tracking is one of the most common uses of RFID. Companies can put RFID tags on assets that are lost or stolen often, that are underutilized or that are just hard to locate at the time they are needed. Just about every type of RFID system is used for asset management. NYK Logistics, a third-party logistics provider based in Secaucus, N.J., needed to track containers at its Long Beach, Calif., distribution center. It chose a real-time locating system that uses active RFID beacons to locate container to within 10 feet.
Manufacturing
RFID has been used in manufacturing plants for more than a decade. It’s used to track parts and work in process and to reduce defects, increase throughput and manage the production of different versions of the same product.
Supply Chain Management
RFID technology has been used in closed loop supply chains or to automate parts of the supply chain within a company’s control for years.
As standards emerge, companies are increasingly turning to RFID to track shipments among supply chain partners.
Retailing
Retailers such as Best Buy, Metro, Target, Tesco and Wal-Mart are in the forefront of RFID adoption. These retailers are currently focused on improving supply chain efficiency and making sure product is on the shelf when customers want to buy it.
Payment Systems
One of the most popular uses of RFID today is to pay for road tolls without stopping. These active systems have caught on in many countries, and quick service restaurants are experimenting with using the same active RFID tags to pay for meals at drive-through windows.
Security and Access Control
RFID has long been used as an electronic key to control who has access to office buildings or areas within office buildings. The first access control systems used low-frequency RFID tags. Recently, vendors have introduced 13.56 MHz systems that offer longer read range. The advantage of RFID is it is convenient (an employee can hold up a badge to unlock a door, rather than looking for a key or swiping a magnetic stripe card) and because there is no contact between the card and reader, there is less wear and tear, and therefore less maintenance.
As RFID technology evolves and becomes less expensive and more robust, it’s likely that companies and RFID vendors will develop many new applications to solve common and unique business problems.
RFID Emblem
In order to provide a simple, visual guide to identify RFID-enabled labels and tags, AIM developed the AIM RFID Emblem™ and submitted it to ISO for incorporation into an international standard – ISO/IEC 29160 (published in June 2012).
The RFID Emblem International Standard specifies the design and use of the RFID Emblem: an easily identified visual guide that indicates the presence of radio frequency identification (RFID). It does not address location of the RFID Emblem on a label. Specific placement requirements are left to application standards developers.
ISO 29160 – RFID EMBLEM EXAMPLE
The RFID Emblem provides a visible identification method for RFID transponders, interrogators, and tagged items. Visible signs inform consumers whether an item or product contains an RFID tag. Therefore, this meets one of the main requirements for consumer privacy protection.
The RFID Emblem is a public-domain object intended to augment rather than replace other emblems and logos such as recycling and CE. The RFID Emblem requires no fee for use nor does it have any membership or other use restriction or requirement, other than compliance with this International Standard.
This standard includes an RFID Index, a two-character code which can be included in the RFID Emblem graphic, which provides specific information about compliant tags and interrogator/encoders.
Successful reading of RFID tags requires knowledge of the frequency, protocol and data structure information provided by the RFID Index.